When you are working with JAVA applications and JAVA based server, you may need to configure a Java key store (JKS) file. Self signed keystore can be easily created with keytool command. But if you have a private key and a CA signedcertificate of it, You can not create a key store with just one keytool command.
Generate a Java key pair and keystore: keytool -genkey -alias mydomain -keyalg RSA -keystore keystore.jks -keysize 2048. Generate a certificate signing request (CSR) for an existing Java keystore: keytool -certreq -alias mydomain -keystore keystore.jks -file mydomain.csr. Generate a keystore and self-signed certificate. Keytool –printcert –v –file mydomain.crt. Java Keystore Certificate Check. Keytool –list –v –keystorekeystore.jks. Check a Particular Keystore Entry Using an Alias.
You need to go through following to get it done.
Step 1. Create PKCS 12 file using your private key and CA signed certificate of it. You can use openssl command for this.
Keytool View Jks
If your private key has a password, It would promote to enter the password of private key. You need to define a password for PKCS 12 file as well.

As an example, say i have a private key called “server.pem” and certificate with “servercret.pem”
Step 2. Create JKS file using keytool command
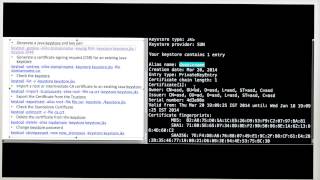
Created PKCS 12 file has been given as the source keystore and new file name (wso2carbon.jks) has been given as the destination keystore.
As an example,
As an additional steps, you can change the private key password of the created JKS file and also the alias name for your private key entry.
Step 3 (Optional). Changing the password of private key file in keystore. More details from here as well
Keytool Create Jks
Step 4 (Optional). Change the alias name of the private key entry
Keytool Create Jks Keystore
By default [current alias] is set to “1”
Keytool Jks Command
Thanks for reading…!!! Also you can find more details on creating self signed KeyStore from here
Related posts:
To Create a CSR with keytool and Generate a SignedCertificate for the Certificate Signing Request
Perform the following operations from the command line.
Generate the Certificate Signing Request.
Generate a signed certificate for the associated Certificate SigningRequest.
Use the keytool to import the CA certificate into the client keystore.
Use the keytool to import the signed certificate for the associatedclient alias in the keystore.
Caution –The following error will be generated if there is no certificatechain in the client certificate.
This error is because the CA’s certificate was not imported intothe KeyStore first. You must import theCA's certificate (step 4), then import the client.cer file itself to forma certificate chain (step 5).
Now that we have a private key and an associating certificate chainin the KeyStore clientkeystore, we canuse it as a KeyStore for client (adapter)authentication. The only warning is that the CA certificate must be importedinto the trusted certificate store of the web server to which you will beconnecting. Moreover, the web server must be configured for client authentication(httpd.conf for Apache, for example).